Each objective lists specific artifacts (projects, papers, demos) that support it.
Click a card or nav item to jump to proof or notes.
Objective 1:
Create a network infrastructure design communications document that includes identified hardware components, connections to the outside world, identified physical layer connectivity (media) and addressing, including operational and security components in the design.
-
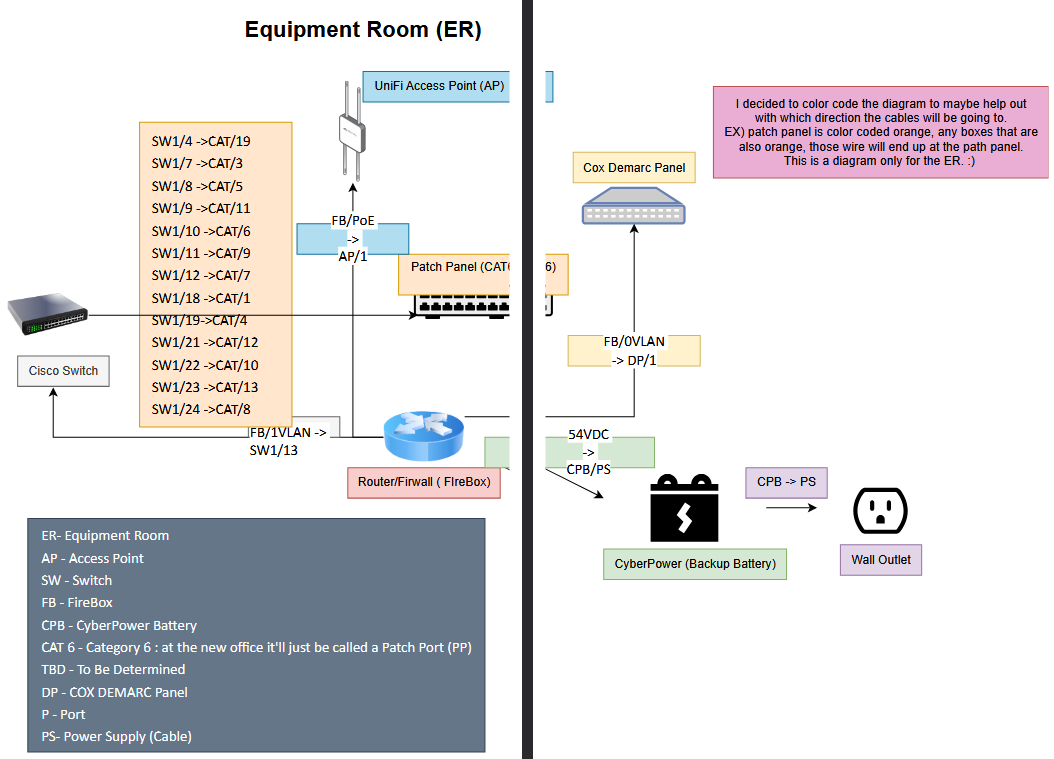
This is a diagram I made based on the server room of my internship. It shows the switch,
patch panel, access point, backup battery, firewall/router, and demarc panel. It also shows the
cable connections to each piece of equipment that was current to their server room.
-
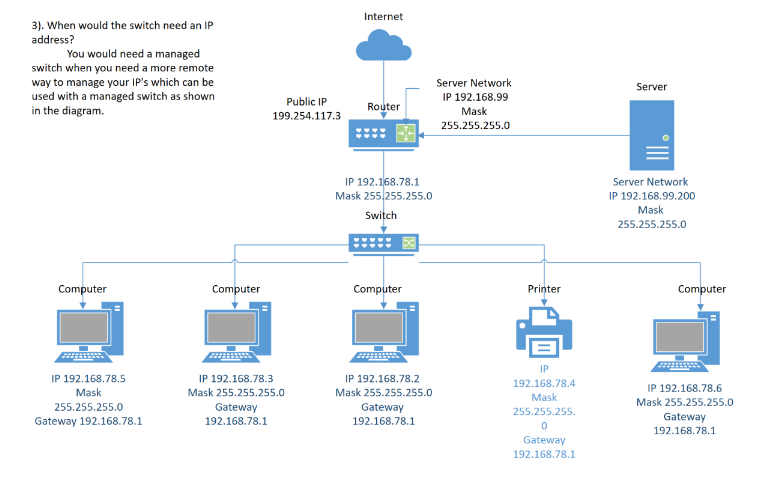
This network diagram shows a simple network that can be seen in the real world, with basic
components such as the cloud/internet, router, switch, computers, printer, and a server with
assigned IP addresses.
Objective 2:
Install, configure and test security hardware and software tools with supporting documentation such as port scanners, vulnerability detection systems, intrusion detection systems, firewalls, system hardening, anti-virus tools, patch management, auditing and assessment.
-
For this project, I utilized TryHackMe to learn different methods of hardening a router through the OpenWrt web interface. I go through steps of setting up the device, changing default credentials, enabling secure network protocols, disabling unnecessary scripts, updating firmware, managing traffic rules, etc.
-
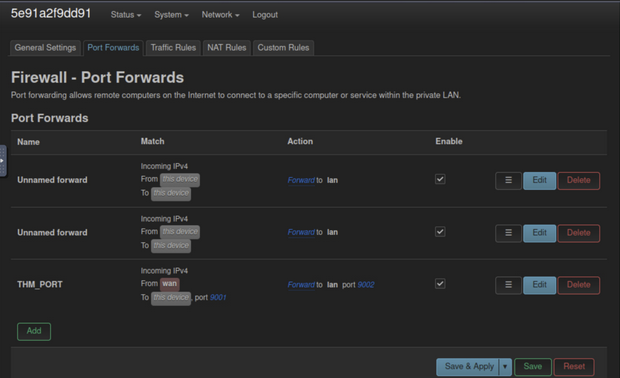
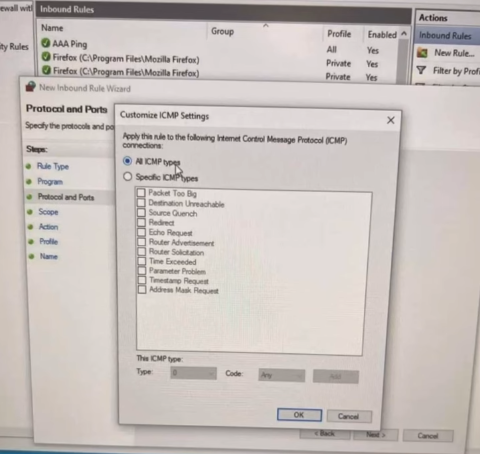
For this project, I created an inbound traffic rule to block inbound connections, created an in bound traffic rule to block ICMP response, and configured Advanced Security Logging based upon best practices to optimize protection for devices in a network. This will allow for review of connection history and provide insight into system activity.(NTS201 Security Essentials)
Objective 3:
Construct, implement and document a script or a program to automate a security-related process or other tasks such as installation, administration, management, mapping resources, logon scripts, patch management, updates, auditing, analysis and assessment.
-
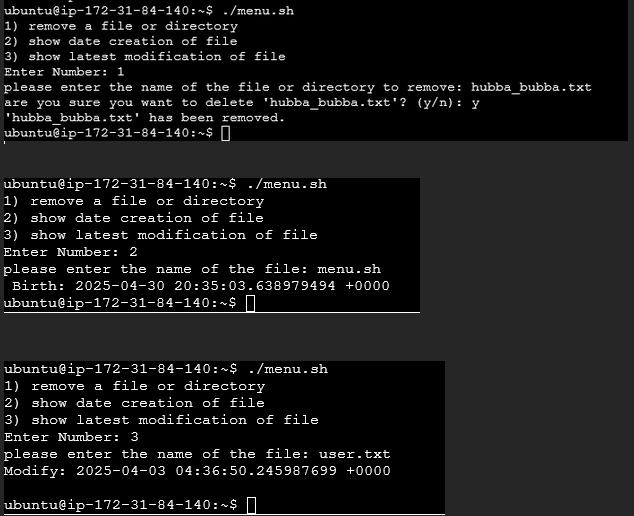
I created a basic script that allows a user to input a number and able to use some actions such as removing a file or directory, showing the creation date of a file, and showing the latest modification of a file through a menu like format.(NTW220 Linux 1 for Technoligists)
-
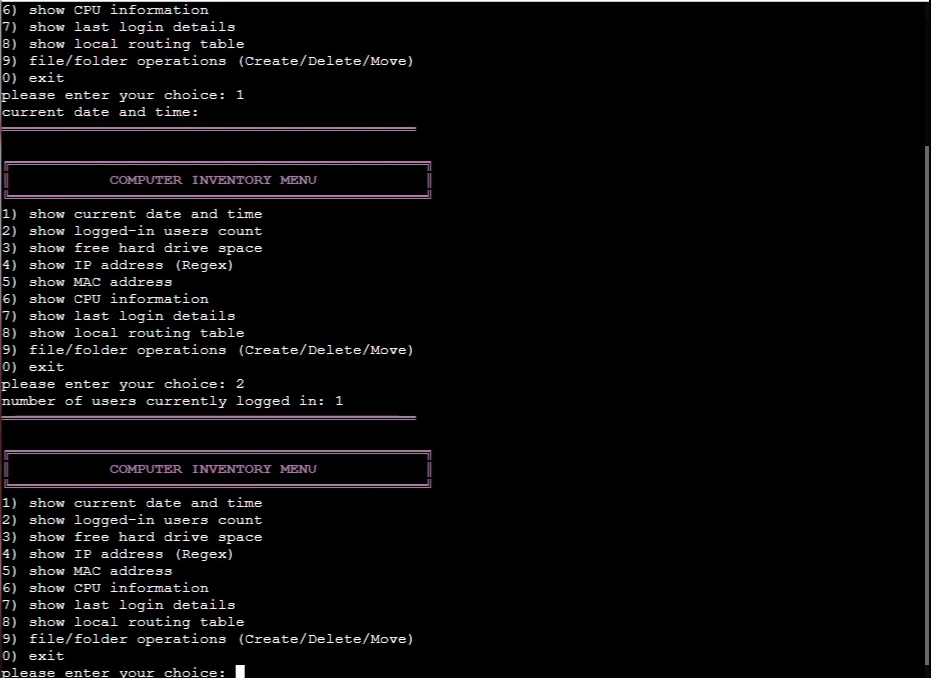
For this project, I created a more user friendly menu script that allows a user to show current date and time, logged-in user count, free hard drive space, IP & mac addresses, CPU information, last login details, local routing table, and create/delete/move files and folders. Along with prompting the user for questions to get the right information for the action. (NTW220 Linux 1 for Technoligists)
Objective 4:
Create a policy or procedure that addresses events such as: a disaster recovery plan, a business continuity plan, an incident response policy, an acceptable usage document, an information security policy, a physical security policy, assessments or troubleshooting procedures
-
I created a security program implementation plan for a fictinal organization's new data center. This data center was going to be one of the largest in the organization's western region and was going to store sensitive customer information that is critical to the organization continuing growth. I outlined three major security controls that I thought the data center could use or take advantage of while also defining what each of them do, purpose and how they are used.(NTS201 Security Essentials)
-

This document shows the troubleshooting steps I took when trying to reconnect a Zebra printer into the network and to work wirelessly throughout the office from any desktop device. I used official Zebra documentation and resources and continued with opening a case number and talking to support to fix the issue. (Internship)
-
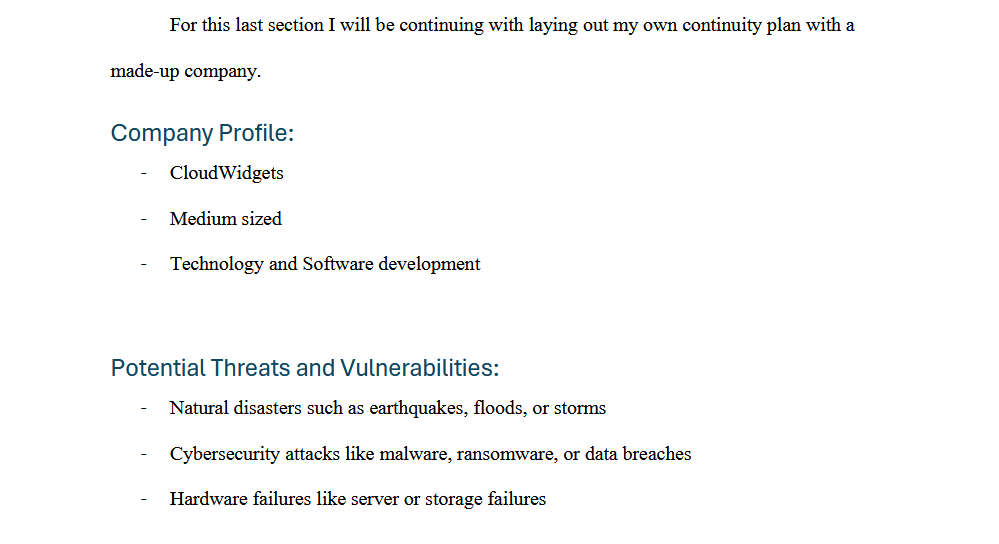
I designed a continuity plan for a hypothetical company by defining potential threats and vulnerabilities, proposing AWS solutions to mitigate the potential risks, and discussing how the provided solutions align with the five pillars of AWS.
-
In this project, I familiarized myself with AWS support infrastructure through exploring their support page and resources, where to file a bug or service ticket, exploring AWS documentation for solutions on specific AWS products/services (NTW216 – System Administration I)
Objective 5:
Develop a research report or implementation plan concerning legal and ethical best practices and mandated requirements that pertain to information security.
-
For this project, I created an INFOSEC Implementation Plan based on SP 800-40 Procedures for Handling Security Patches, August 2002. I outlined what are security bugs, what is the purpose of security patches, problems due to not keeping up witch patches, proposed solutions, equipment and personnel for effective patching, implementation timepline, budget, evaluation system, and the benefits. (NTS435 International and Federal INFOSEC Standards and Regulations)
-

For this project, I creeated an Security Awareness PLan that discussed the key elements and questions that are needed to form a security awareness plan, specific issues the plan will address such as the inclusion of education for different cyber threats, tailored security awareness to employee roles, secure password policies and multifactor authentication, vulnerability testing, etc.I also go over the benefits and drawbacks of the proposed plan (NTS435 International and Federal INFOSEC Standards and Regulations).
Objective 6:
Research, document, test and evaluate several current industry information security-based threats, risks, malicious activities, covert methodology, encryption technologies, mitigation techniques or unconventional tactics to prevent loss of sensitive information and data confidentiality, integrity and availability.
-
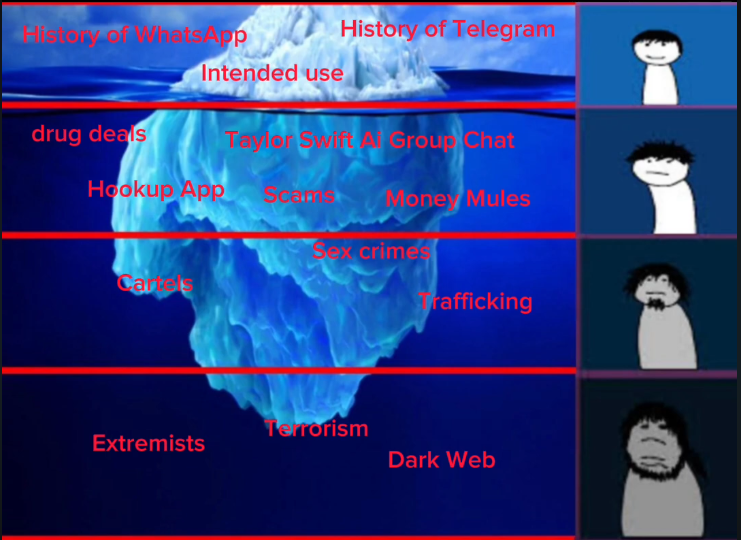
For this video project, I delved deep into the ethics, and malicious activity that is taking place on enryption messesing apps like Telegram and WhatsApp. I presented this in a "Iceberg" format, going through the history of Telegram and WhatsApp and their intended use, AI group chats, scams, drug deals, cartels, trafficking, extremists, terrisom, the dark web, etc. Throughout the video I show sources and real world cases of these topics while also trying to decide whether it is ethically wise to keep encryption based messesing apps. (TCH310 Technology, Society, and Ethics)
-

From visual inspection, main components, identification information, hardware, wireless communications, security features and any mitigations and recommendations about the device. (NTW233 – IoT Architecture)